Smart Barcode Scanning System
Barcode Scanner App for iOS and Android
The barcode scanner app can be installed on smartphones, tablets or rugged mobile computers to scan barcodes, collect additional data and sync all the data to the cloud or your database.
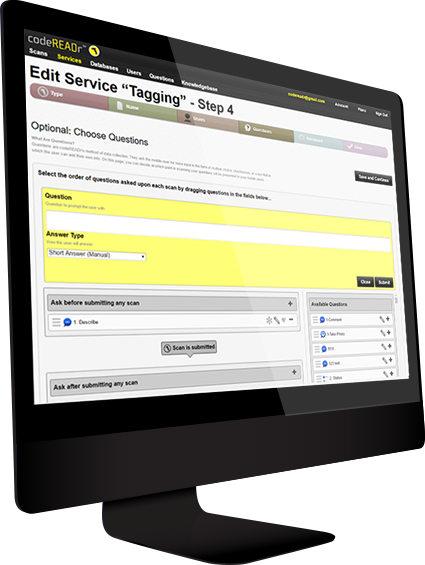
Cloud-based Management Portal
The cloud-based system serves as a centralized hub for managing app users, setting up data collection processes for barcode scanners, and seamlessly handling the storage, organization, export, and integration of scan data with other business systems.
No credit card required to start scanning.
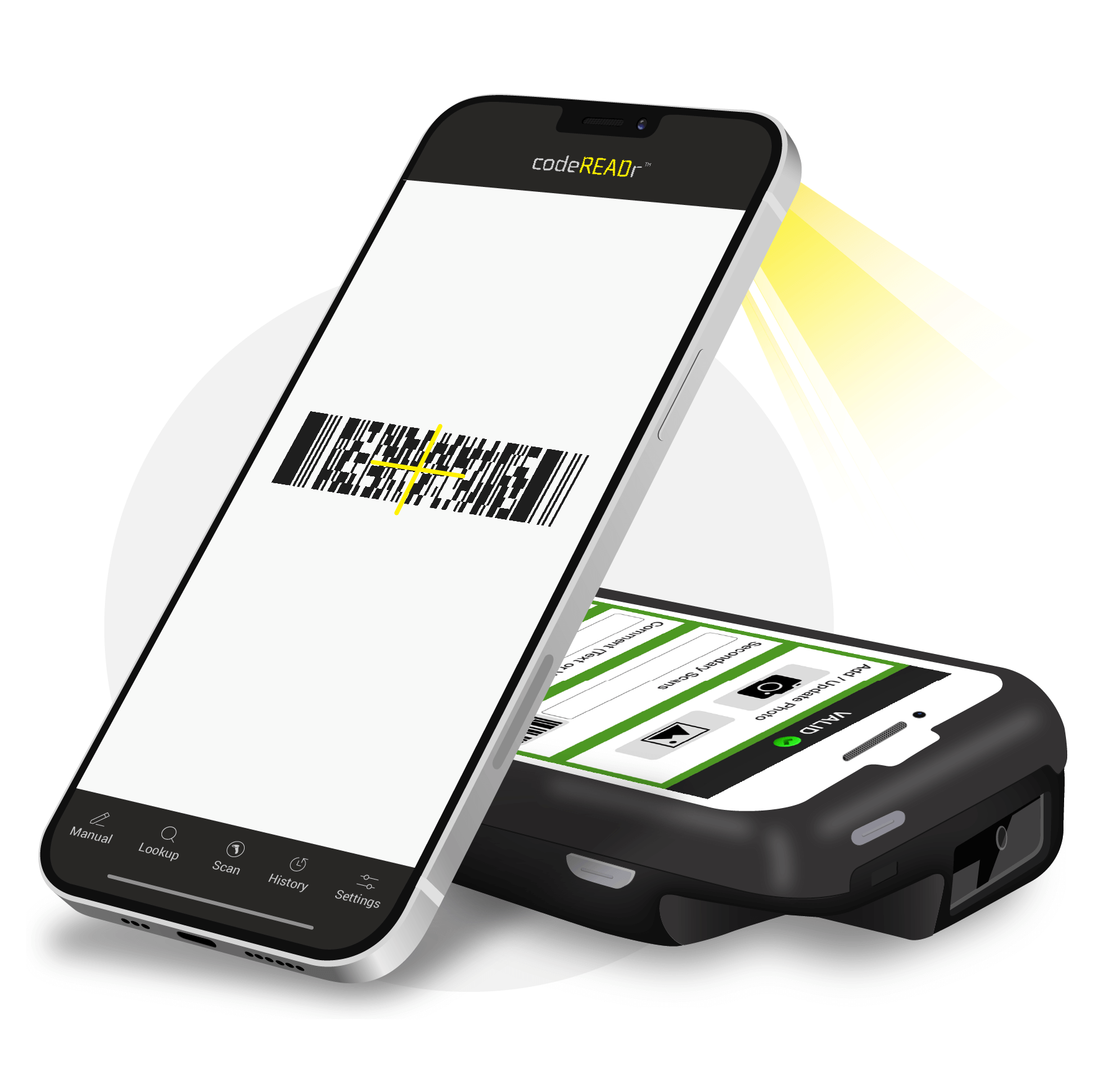

Scan Barcodes, Validate & Connect Data
Scan barcodes and collect data effortlessly with the mobile app. Validate scan data against an existing database. Send scan data to the cloud where you can export in a CSV format, post to your server automatically, or retrieve using the developer API. The scans can also be sent directly to your server.

No Coding Required to Configure
There is no coding required to quickly configure barcode scanning workflows in the cloud based management portal. You can configure multiple service workflows for your business and assign them to specific app users. The cloud-based system supports many solution configurations.
Supports a Wide Variety of Device Types
Use the app with smartphones, tablets, scan sleds, and Android based mobile computers. Scan barcodes with the built-in camera, a hardware imager or a Bluetooth barcode scanner.

iOS and Android OS
Smartphones

iOS and Android OS
Tablets

iOS and Android OS
Scan Sleds

Android OS
Rugged Mobile Computers

Android OS
Chromebooks

iOS and Android OS
Bluetooth Scanners
Barcode Scanner App for iOS and Android

Cloud-based Management Portal and Barcode System